Cyber Resilience Act: new EU requirements for product cyber resilience
The Cyber Resilience Act – the EU regulation on cyber resilience – introduces new requirements for products, processes and documentation. Get an overview of the regulation and what it means for you.
Cyber resilience will soon be a legal requirement in the EU
The regulation of cyber and information security is one of the areas the European Commission has focused heavily on in recent years. The regulations are now nearing completion, and it will not be long before they enter into force.
NIS2 (the Directive on Security of Network and Information Systems) is one of the directives that has attracted the most attention in this context. However, NIS2 concerns organisations – what about general products?
On 23 October 2024, the so-called Cyber Resilience Act (CRA) was adopted in Europe. This regulation lays down a number of essential requirements that products must meet to be placed on the internal market in the EU, if they fall within its scope.
The Cyber Resilience Act applies to products with digital elements
The CRA applies to products with digital elements that can be connected to other devices or networks. Article 2.1 of the regulation states:
“This regulation applies to products with digital elements made available on the market, the intended purpose or reasonably foreseeable use of which includes a direct or indirect logical or physical data connection to a device or network.”
Article 3.1 defines ‘products with digital elements’ as:
“a software or hardware product and its remote data processing solutions, including software or hardware components being placed on the market separately.”
In other words, these are products capable of communicating data. The regulation text includes additional descriptions and definitions of the various elements.
When does the Cyber Resilience Act enter into force?
2 dates are particularly important for manufacturers and suppliers in relation to the Cyber Resilience Act:
11 September 2026
This is when the manufacturer’s reporting obligations take effect. It means that manufacturers must notify the authorities when they discover exploited vulnerabilities in their products.
11 December 2027
This is when the requirements for the products themselves take effect. From this date, products may only be marketed in the EU if they comply with the new rules.
Requirements and classification of products in the Cyber Resilience Act
The essential cyber resilience requirements that products must meet are divided into 2 categories:
| Processes | Product |
|
|
Table 1 – Essential requirements for products with digital elements
This means there are requirements for both the products and the organisations that manufacture, import and distribute them. Note that the requirements apply to the product throughout its lifecycle, not just when it is placed on the market. This means you are obliged to support the security of the product for as long as it is marketed.
For covered products, three categories are specified, determining the available options for conformity assessment: general, important and critical. This is specified in Articles 7 and 8 of the regulation, which define the criteria for important and critical products.
Certain general criteria must be met for products to be considered important or critical, and the product must fall under a general product category, such as operating systems, routers, firewalls, smartcards etc.
Note that important products are further divided into class I and class II. Products that cannot be classified as important or critical fall under the “general” requirements.
How is conformity assessed?
The requirements for the product and its maintenance apply regardless of how the product is classified. The difference lies in the available conformity assessment procedures.
In general, one can choose between 3 different methods of conformity assessment – also called modules:
- Module A: Self-assessment, where the manufacturer itself evaluates whether the product meets the essential requirements. This may be supported by relevant standards.
- Module B + C: Third-party assessment, where a notified body (NB) tests a sample. If approved, this sample will be used as the reference for the rest of the production.
- Module H: Assessment of the manufacturer’s quality assurance system. A notified body checks whether the system ensures all products meet the requirements.
In addition, an EU-certified certification scheme may be used for the relevant product type.
Standards make it easier to meet the requirements of the Cyber Resilience Act
Most manufacturers use either Module A (self-assessment) or Module B+C (EU type approval). In both cases, using relevant standards can be a significant advantage.
Standards can provide an indication of what is considered state-of-the-art for the product in question, and what tests or assessments are relevant to carry out – as well as how they should be performed. They also help ensure a more uniform and consistent assessment across product families.
Assessment methods in the CRA
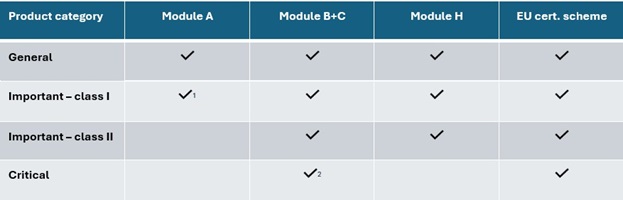
1 Only when using harmonised standard
2 Only if relevant certification does not exist
As Table 2 shows, harmonised standards will be required for the 19 product types under “Important – class I” if self-assessment is to be possible.
It will also be beneficial to have standards covering the general essential requirements for both general and critical products, as this can help manufacturers identify the actions required to meet the essential requirements.
How standards are developed for the Cyber Resilience Act
To meet the need for documentation and conformity, the European Commission has requested the European standardisation organisations (ESOs) to develop no fewer than 41 standards to cover the essential requirements of the regulation. The standards are divided into 3 groups:
- 14 horizontal standards on security requirements related to properties of products with digital elements
- 1 horizontal standard on vulnerability handling
- 26 vertical standards to cover each category of important and critical products.
The starting point for the standards is:
- Annex I of the regulation – for the horizontal standards
- Annexes III and IV – for the vertical standards, which relate to specific important and critical products.
The request has been sent to the 3 ESOs: CEN, Cenelec and ETSI. The requested standards are distributed among the relevant committees of the ESOs. A large portion of the vertical standards are handled by ETSI, and the horizontal ones by Cenelec.
At present, work is underway to develop basic standards that may cover one or more parts of the horizontal standards, and to identify existing standards that may be used for the vertical ones.
Some of the requested standards – those concerning critical product types – are being developed in closed forums. Only experts from organisations established in the EU and stakeholders representing EU interests can participate.
In general, standards are developed by experts in the relevant field through a defined process that meets the requirements of Regulation 1025/2012, which specifies requirements for transparency, stakeholder participation and procedures.
FORCE Technology’s role in the standardisation work
The standards to be developed for the CRA cover a wide range of products. Some must be general, others specific, and some cover only a single product type. This means that both generalists and specialists are needed to ensure that the standards are of high quality and appropriate for their intended use.
Experts from FORCE Technology and other GTS institutes participate in several committees and working groups. The aim is to ensure that the standards produced are understandable for Danish companies and best describe the level of security the CRA aims to achieve. At the same time, the standards must improve product security in the EU and make European products competitive in the international market.




